Is your OpenCart admin panel being DDoS attacked?
We have recently seen a surge of what appear to be brute-force attacks from all over the world, targeting any and every website they can - including OpenCart sites. The first symptoms are a sudden huge drop in website speed in both the storefront and admin panel, as well as pages failing to load entirely with errors such as connection timed out and max_user_connections exceeded.
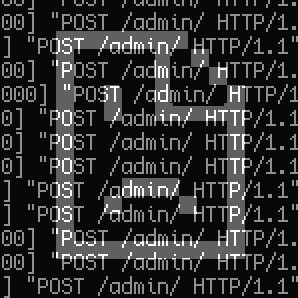
The key sign that your website is affected by this particular attack is in your server access log. Here's an example from one website which was targeted by this attack:
18.130.230.142 - - [24/Jan/2022:09:31:44 +0000] "POST /admin/ HTTP/1.1" 200 1629 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 35.77.98.144 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1627 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 3.96.133.239 - - [24/Jan/2022:09:31:44 +0000] "POST /admin/ HTTP/1.1" 200 1628 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 52.198.190.2 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1629 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 3.83.49.191 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1626 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 3.25.52.200 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1629 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 54.157.212.69 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1628 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 15.228.78.166 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1626 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 52.13.59.17 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1628 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0" 3.124.117.161 - - [24/Jan/2022:09:31:45 +0000] "POST /admin/ HTTP/1.1" 200 1630 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"Heaps of requests to the /admin/ page every second! This is only a ten-line sample of an enormous 700,000-line-long access log for that day alone. That's a lot of unfriendly traffic!
The data sent in these requests almost universally contains a username of admin and a very simple password - usually a word or name and maybe one or two numbers - indicating this is actually a form of dictionary attack, where bots will send hundreds of login attempts to a server, trying out a huge list of common passwords one-by-one in an attempt to find one that will let them break into your admin panel (this is also why it's important to use a strong password that's hard for bots to guess!).
Luckily, we at Antropy have developed a handy extension that will stop these nasty bots in their tracks. To help as many in the OpenCart community as possible to secure their sites, we have made it available for free download on the OpenCart Marketplace.
Download the Antropy Admin Panel Brute Force Block extension
If you would like us to install this extension on your site for you, send us an email at info@antropy.co.uk and we will be happy to help. If your website is hosted on our servers we can put additional measures in place to further keep these spammers at bay and ensure your website's in top shape for your customers.