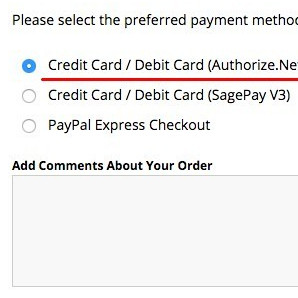
OpenCart Checkout Hack Authorize.net
We have recently been contacted by several different companies (some existing clients, some totally new to us) who have noticed extra payment gateways or errors on the checkout. This unfortunately is a tell tale sign that the site has been hacked. In almost all of these cases the attacker has modified either the authorize.net (aim) or PayPal Pro payment gateways to harvest customer credit card information.
The attackers will almost always leave additonal backdoors dotted around the site which can be very tricky to detect. These can include:
- Modifying the admin login procedure to email admin credentials to an email address.
- Adding a master password to allow them access to the admin without a user account.
- Hiding simple html forms which allow them to upload files or execute commands on the server.
We have come across many other examples (some which are extremely clever).
What to Look Out For
- Payment gateways in the checkout which you haven't enabled.
- A message at the top of the site saying something like "merchant ID disabled".
- Customers alerting you that their card details have been stolen.
- Missing payment gateways (specifically authorize.net (aim) or PayPal pro) on the Extensions > Payment page.
How did they get in?
It's almost impossible to say after the event, but we think it's likely to be weak passwords rather than a vulnerability in OpenCart itself. Password cracking has become significantly better in recent years, so you must use a VERY strong password as described in my blog article here:
https://www.antropy.co.uk/blog/are-passwords-with-numbers-instead-of-letters-secure/
If you do have raw server access logs that go back far enough, an experienced developer / security expert may be able to determine exactly how they got in by looking at what incoming requests were made to the server around the time that files were modified.
You're Not Alone
You can see from the OpenCart forum threads below that it has affected lots of people and although it is a terrible thing and you should increase your security, it's very clear from the news these days that no one is immune from hacking, so rather than feel guilty you should fight back with stronger security and let your customers know ASAP. Unless your passwords were all "admin" or "password" it probably wasn't entirely your fault.
OpenCart Forum Related Topics
- https://forum.opencart.com/viewtopic.php?f=20&t=144753
- https://forum.opencart.com/viewtopic.php?t=147282
- https://forum.opencart.com/viewtopic.php?f=190&p=735918
- https://forum.opencart.com/viewtopic.php?t=162677
What to do next?
- Put the site in to maintenance mode so no one else is affected.
- Remove all malicious code - easier said than done, it tends to take us 1/2 day or more.
- Change all passwords: FTP, hosting control panel, OpenCart admin, database.
- Find out which customers placed orders since the offending files were modified and let them know what happened.
- Make sure you're running the latest version of PHP as ~5.3 had a vulnerability that allowed hackers to upload a file.
- Install some method of monitoring your site for file changes - we offer a piece of software to do this - get in touch to find out more.
- Once you're sure all malicious code has been removed, re-enable the store.
- Report it here https://www.actionfraud.police.uk/report-a-fraud-including-online-crime
Update 2019-07-29
Since being approached by quite a few store owners to urgently help with hacked websites, we formed a partnership with Astra who specialize in website security and are better set up to respond.
They have written this great article on the payment method hacks described above and we recommend that you contact them immediately if your website has been hit by this attack via their contact page: Contact Astra
blog comments powered by Disqus