How To Lock Down Your OpenCart Site in Case of a Hack
It is hard to find reliable answers to pressing questions like, what steps to take to minimize the damage to your OpenCart site on the web.
Before you can even begin to clean your hacked OpenCart site, it is vital that you lock it down from further damage. Locking your site properly also helps in preventing contamination to other websites on the same server.
To help you with the process, we've written this article.
After reading this article, you will primarily be able to minimize damage to your hacked OpenCart store.
Even if you come to know of your hacked site pretty late, locking it down will still help you in cutting all access links that the hacker might have.
To confirm that your OpenCart site is indeed hacked, check the symptoms in the following segment.
Signs Indicating Your OpenCart Site is Under Attack
These are some symptoms that strongly indicate that your OpenCart site is hacked:
1. Credit Card Hack
If your customers complain to you about their credit card being misused, it is a huge sign that your website might be hacked.
Generally, there are two ways by which hackers steal credit card details:
- By inserting JavaScript in the checkout page.
Hackers inject malicious JavaScript that steals credit card info from the checkout page. Click here to know more about how & where hackers inject JS in your OpenCart store. - By changing or adding a payment method in the checkout page of the store.
This is when an intermediary fake form is added between your checkout page and your payment gateway. Basically, customers never get to your authentic payment gateway and swipe their cards on the fake form.
To learn more about the Authorize.net hack, click here.
Other OpenCart hack symptoms are Redirection, SEO spam or Admin panel hack (or defacement).
2. Unknown SQL Requests
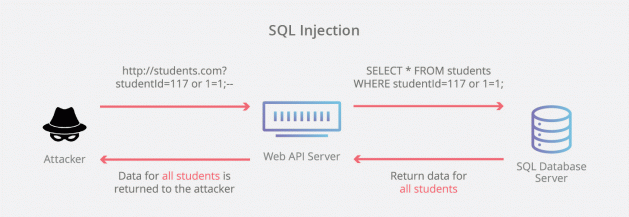
SQL Injection has been a popular attack vector for attackers in order to hack a site. OpenCart uses MySQL as its database management system. Thus, it becomes essential that you regularly check your MySQL log file. Any SQL Request that seems unfamiliar or malicious must raise a red flag. These requests may be leaking all keys from a table or leaking all table names from a database.
If you see them that means the attacker has access to your database and will leverage this to attack your customer's personal data.
3. Several requests from a single IP

The attacker in order to exploit your site must explore its attack-surface, he/she will achieve this from scanning your OpenCart installation with the help of automated tools sending a huge amount of traffic to your site for a small period of time and from a single IP.
High network traffic also could indicate a DDOS attack at your site or a Brute Force attack. Nonetheless, it must be read as a warning for you.
4. Several Failed Login Attempts
If you see several failed login attempts at your site in a short period of time, that is an indication that your site has experienced a brute force attack.
In such a case, you may want to change all the user and admin account passwords of your OpenCart account.
4. Requests to Non-Existing Pages
Attackers use a technique called directory brute forcing or dir-busting. In this, they send several HTTP Get requests to import directories or files that may have been exposed in order to leverage them for an attack.
Thus, if you see various requests to non-existing directories or files, you must block the IP from which the request is emerging from and thus avoid an attack.
5. XSS attacks (Cross-Site Scripting)
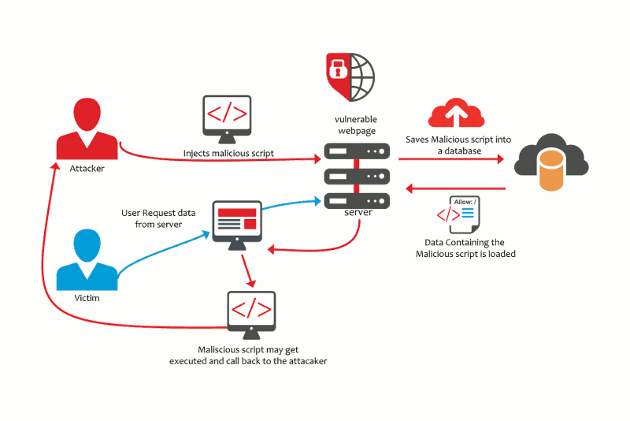
A Cross-Site Scripting (XSS) attack occurs when the attacker is able to inject and execute malicious JavaScript code on your website. These attacks are hard to detect as the injected JavaScript code is executed in the user's web browser instead of the website server.
With this attack, if successful, the attacker can steal credit card information from the payment page, user's personal information and can even deface the website.
In order to detect these kinds of attacks, you must scan your website's source code for any kind of stored XSS payload and must have it scanned regularly for XSS vulnerabilities.
Locking Down OpenCart
Understanding that your OpenCart Website is under attack was the first step towards stopping the attack. Most website owners aren't even aware that their site was hacked until it too late. Once you are aware that your site is under attack you must take vital steps to stop the attack.
1. Turn on Maintenance Mode
You should start by putting your OpenCart installation in maintenance mode. The maintenance mode allows only admin to access the OpenCart site and manage its features.
It is a step important to do as it limits the attacker's ability to affect the user and cause more damage to the sites' reputation. To put your OpenCart site under maintenance mode follow these steps:
- Login as admin into your OpenCart Dashboard
- Select System then Settings
- Select the store and then on click Edit
- Click on the Server tab
- Click on maintenance mode and enable it.
- And finally, click on Save.
2. Asses The Damage
Now once you have the OpenCart site offline from all the users and potential attackers, the first thing you must do is assess the damage.
The attacker could have done a number of things, these may include changing the existing pages, creating new phishing pages hosted on your site, or leaving backdoors to allow them to get access to the site even after the password is changed.
You can do so by the following methods:
1. Referring to an Old Backup
If you have been taking regular backups of your site, now is when it comes into play. Regular backups play an important role when checking what damage had been done to the site and its database in case of a hack.
You should start assessing the damages that occurred by comparing your current OpenCart installation to an old reliable backup you made of your site. Keep an eye for the following:
- Newly created pages.
- Modification to code on PHP scripts or javascript scripts.
- Added information in the MySQL database.
- Newly created redirect links to malicious pages.
- Cron jobs that were created during the course of the hack.
2. Checking the Error Logs
You should also read the error logs. They contain interesting information that can be used to figure out what areas of the web-application were attacked and help you find the vulnerability that was exploited in the hack and if any backdoor was created during the process.
In the Apache server and most other web servers, the error log file is generally stored in the system/logs/ directory. You should look out for failed login attempts, permission denied and other things that stand out.
3. Change Passwords
Once you have recovered your site from the hack, have fixed the vulnerability and have removed the backdoor that may have been installed on your web server, congratulations you are about 75% done and have survived this cyber crisis. But, the work is not 100% done yet.
It recommended changing the admin password and all user passwords on the OpenCart installation as it is possible the hacker may have those and can gain authorization again. To change the password on OpenCart follow these steps:
- Log into your OpenCart Dashboard.
- Go to System > Users > Users.
- Select the administrative user you employ and click "Edit"
- Type your new password in the “Password” field.
- Re-type your new password in the “Confirm” field.
The method to change password may vary with the version, if you don't find this useful you should refer to the OpenCart Documentation.
4. Block Any Malicious IP Address
Using the .htaccess file
The .htaccess file in a configuration file that controls how your server will respond to requests from various IPs. You can edit your .htaccess file with the help of the following step.
- Open your OpenCart installation root folder.
- Now edit the .htaccess file (if you don't find one just create a new one)
- In the file, you can deny access to the website for an IP by using the keyword Deny. You can specify a specific IP or a range of them.
Deny from xxx.xxx.xxx.xxx
Deny from yyy.yyy.yyy.yyy/zz (subnet)
Note: Replace "xxx.xxx.xxx.xxx” and other with your admin IP.
You can also use this method the other way round. Instead of denying access, you can allow specific IP/IP range to access your OpenCart website.
Just add the following command in your .htaccess file:
Allow from xxx.xxx.xxx.xxx
Allow from yyy.yyy.yyy.yyy/zz (subnet)
Note: Replace "xxx.xxx.xxx.xxx” and others with your admin IP.
In order to deny allow access to all IPs to your site except yours i.e. the admin IP add the following to your .htaccess file:
Order deny, allow
Deny from all
Allow from xxx.xxx.xxx.xxx
Note: Replace "xxx.xxx.xxx.xxx" with your admin IP.
Now only you can access your site (via admin IP) and a full lockdown is achieved.
- Root out and delete all vulnerable scripts in your Administrative area.
- Install script to not only lockout hackers & hacker bots, but also to trap them.
Get Expert Help
Getting your site hacked can take a major toll on your site's reputation as well as on your business. As it is said prevention is better than cure, you should take measures to secure your site from hacks like this.
For professional help, we recommend Astra Security. They are experts in Opencart Malware Removal & Security.
Conclusion
To sum up, you should lock down your attacked OpenCart store by following these systematic steps. In CyberSecurity reacting to a cyberattack, is called Incident Response. In an unfortunate event of a major attack on your website, you can always get help from security experts.
Additionally, deploying a firewall on the website promises further protection.
Stay Secure!
blog comments powered by Disqus


















